Acquisitions are crucial for business transformation, but the focus on cybersecurity risks in M&A transactions has increased significantly in recent years, becoming a priority for executives. These transactions can indeed generate major risks for IT teams and system security.
This is why the cybersecurity team plays a decisive role in ensuring not only the security of the target environment, but also ongoing protection throughout the program. The latter includes openings of flows or services, migrations (application, network or data) and exemptions.
Security extends to all technical aspects of an M&A&D project, covering the network, work environments and identity management.
So how can we ensure the leading role of cybersecurity in M&A projects?
Let’s take a concrete look…
In 2017, Yahoo disclosed two massive data breaches, affecting approximately 3 billion accounts in 2013 and 500 million in 2014, which had a major impact on its transaction with Verizon. The disclosure of these cyberattacks led Verizon to negotiate a reduction in Yahoo’s purchase price, from $4.83 billion to approximately $4.48 billion, and led to significant adjustments in the terms of the deal to account for the increased risks. This incident highlighted the critical importance of cybersecurity in merger and acquisition (M&A&D) transactions, demonstrating the need for thorough due diligence to assess cyber risks and the potential implications for deal valuation and terms. Lessons learned from this attack continue to shape M&A&D dealmaking and risk management practices.
Strategic priorities: what’s next
In M&A transactions, managing cybersecurity issues is of paramount importance. The top priority is to protect sensitive data from security threats such as cyberattacks and data breaches. It is important to recognize that any breach in this area can result in disastrous legal, financial, and reputational consequences for the company.
In addition, there is a growing need to comply with a growing set of data protection and cybersecurity regulations, such as GDPR and DORA. Assessing these risks during due diligence is essential to avoid the negative consequences of a post-acquisition security breach.
Finally, the importance of managing corporate culture should not be overlooked. The values, norms, practices and behaviors that define the organization are essential to creating a healthy and safe work environment, where cybersecurity is a shared priority for all.
Cyber risks that are starting to gain momentum
- Technology integration during a merger can lead to risks related to unforeseen cyberattacks, particularly due to technology upgrades
- During periods of technology integration, IT resources can be overloaded, which can affect the security and availability of systems
- The M&A process involves the involvement of two sets of critical data, which increases the risks of disclosure or loss of sensitive data
- The disruptions related to adjusting roles and responsibilities to standardize operational procedures and practices can create gaps in system security
- Failure to comply with data protection laws, such as the GDPR, can result in significant fines and litigation
- A poor cybersecurity posture can slow down the acquisition process of the company and, in some cases, compromise the transaction altogether
Cyber roadmap for M&A transactions: key activities at each phase
Integrating cybersecurity into M&A&D requires being included in the right decision circle, having access to information at the right time and being able to share cyber analysis to support the decision-making process.
Below is a general roadmap of cyber activities to be launched in the different phases of an M&A&D transaction and allowing the acquiring company to make informed decisions based on the results obtained.
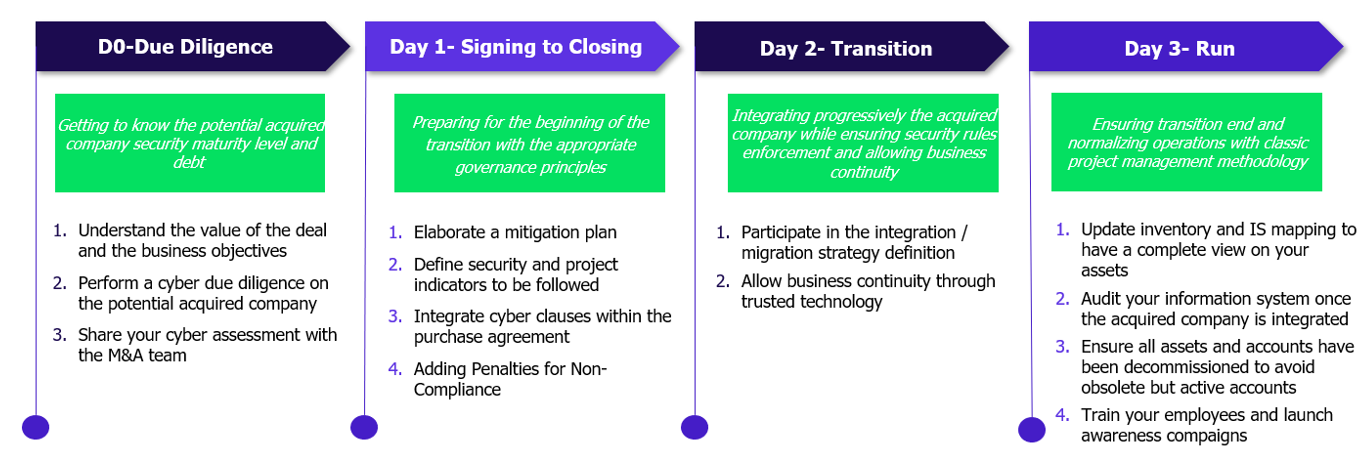
In the context of a merger and acquisition (M&A&D) transaction, the due diligence phase, historically focused on financial and legal aspects, must now include an in-depth assessment of cyber risks. This approach not only allows determining the real value of the target company by identifying its digital assets and vulnerabilities, but also to carry out a complete cyber due diligence, analyzing the information systems, technological infrastructure and existing security policies. These are the principle Key Areas of Evaluation:
- Understand the value of the deal and the business objectives
- Evaluate the security maturity level of the acquired company
- Evaluate the assets, the applications, the data and their sensitivity
- Identify Cyber Risks and Vulnerabilities
- Evaluate the company Response and Recovery Plans
Sharing these results with the M&A team is crucial to inform strategic decisions and adjust the valuation of the transaction according to the risks identified.
Once the agreement is concluded, it is essential to prepare a smooth transition, integrating cybersecurity into contracts and governance plans. This includes developing a mitigation plan to manage the identified risks, setting up security indicators to monitor the effectiveness of the measures during the transition, and inserting specific cybersecurity clauses in the purchase agreement, with penalties in the event of non-compliance.
During the transition phase, the main objective is to integrate the acquired company without disrupting current operations, while ensuring the security of the systems. A suitable integration/migration strategy must be defined, considering the specificities of the target company and the technological differences between the two entities.
Finally, the last step aims to stabilize and standardize operations after the integration. This involves updating the inventory and mapping of the information system, an audit to assess compliance with cybersecurity standards, deactivating obsolete assets, and continuous training of employees to strengthen the security culture. This holistic approach ensures that the business operates in a secure and optimized manner, minimizing long-term risks and ensuring continuous protection against cyber threats.
Conclusion
In the digital age where cyber threats are constantly evolving, proactively integrating cybersecurity into M&A&D transactions is no longer an option but a strategic necessity. This continuous vigilance will be crucial to not only secure the current transaction, but also to prepare the company to face the challenges of tomorrow in an increasingly complex and connected environment. It is imperative to ask: how will cybersecurity due diligence practices evolve to meet emerging threats?



